My usual strategy is to let gmail handle what I'll read by adding a star to those people's emails that I have a personal relationship with, friends, smart people, etcetera; then all I have to do is skim subject lines of unstarred posts before selecting and deleting those (BTW, I star all comments that come in here under the smart people category ;-)). The following almost got cut, but I'm glad it didn't.
An article on Cnet, reports that a Federal Magistrate in the Central District of California has ordered that Torrentspy turn over masked IP addresses in a ongoing civil case that the RIAA brought against it. Why is this interesting? Because the Magistrate ruled that even though the data in RAM is in "electronic storage."
I'm not a lawyer, but let me see if I can put this issue in a nutshell: In criminal and civil cases, there's a pretty well accepted rule; you cannot force someone to create a document that they do not already have, and then force them to produce that document. So, I couldn't send a subpoena to example.com and ask them to produce something worded like this:
"A document containing Customer John Smith's Social security number, mother's maiden name, his last three log ins to the system and his credit card information."
Unless of course, example.com had a document like that already. From the article, "a federal judge in Los Angeles found that a computer server's RAM, or random-access memory, is a tangible document that can be stored and must be turned over in a lawsuit."
What I found most interesting was the discussion of the issue. The Judge's ruling explains some of the history of RAM in Federal court cases, and since there are not a lot of them, I found the analysis enlightening.
You can find the original here, but I have included the discussion below. The case is Columbia Pictures et al. v. Justin Bunneli, et al. CV 06-1093 in the Central District of California

Discusson of Websites in general.

Operation of defendants' website.

Discussion of server log data.

RAM is Electronically Stored Information according to the Federal Rules of Evidence:
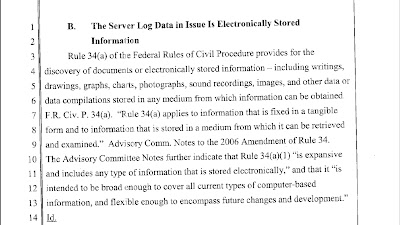
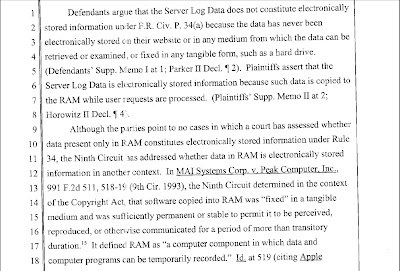
MAI Systems Corporation v. Peak Computer, Inc., 991 F.2d. 511, 518-19(9th Cir. 1993) citation:
Perfect 10, Inc. v. Amazon.com, Inc., 2007 WL 1428632 (9th Cir. May 16, 2007:

Three more cases discussing RAM:

If you read the decision, you see that there are several cases where courts have ruled that data in RAM is both tangible and recoverable. What does all this have to do with forensics? Well, what if you had a case where a kid had been kidnapped after chatting with the bad guy in an Instant Messaging session and there was not any logging of chats?
Assume that you could collect the contents of RAM and find the smoking gun there (say, the offender's IM name) and this led you to the bad guy, and you later discovered that he killed the kid. If you had those kinds of data from RAM, that could be incredibly important to your case. If your evidence came up for a supression hearing, you could point your prosecutor to some other cases where other courts had examined the contents of RAM as evidence, and that might be useful to help put our bad guy where he belongs by helping get the chats you recovered allowed into evidence at trial.



1 comment:
Great post, thanks for pointing this out! Very interesting stuff.
Post a Comment