http://jsunpack.jeek.org/dec/go\\
I haven't mentioned my disdain for all things Java. There it is.
Saturday, February 21, 2009
Tool to list windows protected files
Not tested, but interesting nevertheless: SFCList by Nagareshwar Talekar
From his blog post: After I wrote about ‘Detecting System DLL’ some of my friends working on malware analysis asked for any tool which can show if the particular file is protected by SFC mechanism. I could not find any such tool and decided to write my own tool. . .
From his blog post: After I wrote about ‘Detecting System DLL’ some of my friends working on malware analysis asked for any tool which can show if the particular file is protected by SFC mechanism. I could not find any such tool and decided to write my own tool. . .
Sunday, January 18, 2009
Vanity
I was doing a vanity search today on this page and found that my post "Defeating" whole disk encryption was cited in:
Christopher Hargreaves, Howard Chivers, "Recovery of Encryption Keys from Memory Using a Linear Scan," ares,pp.1369-1376, 2008 Third International Conference on Availability, Reliability and Security, 2008
I haven't read the article, but the abstract sounds enticing:
As encrypted containers are encountered more frequently the need for live imaging is likely to increase. However, an acquired live image of an open encrypted file system cannot later be verified against any original evidence, since when the power is removed the decrypted contents are no longer accessible. This paper shows that if a memory image is also obtained at the same time as the live container image, by the design of on-the-fly encryption, decryption keys can be recovered from the memory dump. These keys can then be used offline to gain access to the encrypted container file, facilitating standard, repeatable, forensic file system analysis. The recovery method uses a linear scan of memory to generate trial keys from all possible memory positions to decrypt the container. The effectiveness of this approach is demonstrated by recovering TrueCrypt decryption keys from a memory dump of a Windows XP system.
Academic respectability. Woot!
Christopher Hargreaves, Howard Chivers, "Recovery of Encryption Keys from Memory Using a Linear Scan," ares,pp.1369-1376, 2008 Third International Conference on Availability, Reliability and Security, 2008
I haven't read the article, but the abstract sounds enticing:
As encrypted containers are encountered more frequently the need for live imaging is likely to increase. However, an acquired live image of an open encrypted file system cannot later be verified against any original evidence, since when the power is removed the decrypted contents are no longer accessible. This paper shows that if a memory image is also obtained at the same time as the live container image, by the design of on-the-fly encryption, decryption keys can be recovered from the memory dump. These keys can then be used offline to gain access to the encrypted container file, facilitating standard, repeatable, forensic file system analysis. The recovery method uses a linear scan of memory to generate trial keys from all possible memory positions to decrypt the container. The effectiveness of this approach is demonstrated by recovering TrueCrypt decryption keys from a memory dump of a Windows XP system.
Academic respectability. Woot!
Tuesday, December 30, 2008
Tubes Clogged, Internets are Broken II
and just to claify, this means that Certificate Authorities using MD5 are broken. Browsers implicitly trust certificates, and to quote:
This ... shows that the certificate validation performed by browsers can be subverted and malicious attackers might be able to monitor or tamper with data sent to secure websites. Banking and e-commerce sites are particularly at risk because of the high value of the information secured with HTTPS on those sites. With a rogue CA certificate, attackers would be able to execute practically undetectable phishing attacks against such sites.
My guess is that this attack will be implemented in the wild in the very near future. . .
This ... shows that the certificate validation performed by browsers can be subverted and malicious attackers might be able to monitor or tamper with data sent to secure websites. Banking and e-commerce sites are particularly at risk because of the high value of the information secured with HTTPS on those sites. With a rogue CA certificate, attackers would be able to execute practically undetectable phishing attacks against such sites.
My guess is that this attack will be implemented in the wild in the very near future. . .
Tubes Clogged, Internets are Broken
The Internets are broken!
Set your system date to August 2004 before visiting the site.
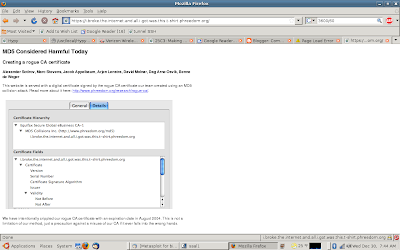
More here and here.
Alexander Sotirov et. al. did some really interesting research on creating a fake CA using 300 playstations - Fear!
Set your system date to August 2004 before visiting the site.

More here and here.
Alexander Sotirov et. al. did some really interesting research on creating a fake CA using 300 playstations - Fear!
Thursday, September 4, 2008
More fun with Chrome
The Sunbelt Blog has a link here that will force Chrome to crash.
Or you can enter crash:% into your browser and do it yourself.
Good times.
Or you can enter crash:% into your browser and do it yourself.
Good times.
Google's Chrome Browsing History, a first pass
This will be a short post. I'm sleep deprived and traveling. . .
Google Chrome debuted yesterday. So sometime this week, someone somewhere will have to do some analysis on Chrome's browser artifacts. Until someone writes a script/program to extract user history, here's one way to get some information:
Chrome saves its data files in C:\Documents and Settings\[user]\Local Settings\Application Data\Google\Chrome\User Data\Default
The following files store data in SQLite format 3:
Archived History
Cookies
History
Thumbnails
Web Data
To examine those data archived in SQLite format 3, you can run strings against the files. I found sqlite3explorer here. This does a fairly decent job of rendering the data.*
IF we open the "history" file and go to main > tables > urls and right click on

urls, we can click "show data" and the bottom right windows will populate with the data in the urls colunm.
It is important to note that Chrome will import browsing history from other web browsers, so the history contained here may not have been generated by Chrome.
Running Strings against the following files will/may reveal interesting data:
Last Session
Preferences
Current Session
Visited Links has binary data. YMMV.
* This doesn't work well on my computer unless executed by double clicking on the icon from the firefox download tab:

There are also files called:
History Index 2008-09
History Index 2008-08
(It appears that these are created daily, but this needs to be confirmed)
Google Chrome debuted yesterday. So sometime this week, someone somewhere will have to do some analysis on Chrome's browser artifacts. Until someone writes a script/program to extract user history, here's one way to get some information:
Chrome saves its data files in C:\Documents and Settings\[user]\Local Settings\Application Data\Google\Chrome\User Data\Default
The following files store data in SQLite format 3:
Archived History
Cookies
History
Thumbnails
Web Data
To examine those data archived in SQLite format 3, you can run strings against the files. I found sqlite3explorer here. This does a fairly decent job of rendering the data.*
IF we open the "history" file and go to main > tables > urls and right click on

urls, we can click "show data" and the bottom right windows will populate with the data in the urls colunm.
It is important to note that Chrome will import browsing history from other web browsers, so the history contained here may not have been generated by Chrome.
Running Strings against the following files will/may reveal interesting data:
Last Session
Preferences
Current Session
Visited Links has binary data. YMMV.
* This doesn't work well on my computer unless executed by double clicking on the icon from the firefox download tab:

There are also files called:
History Index 2008-09
History Index 2008-08
(It appears that these are created daily, but this needs to be confirmed)
Subscribe to:
Posts (Atom)


